S3 Ransomware Attacks: The S3 Heist Nobody's Talking About
Most S3 ransomware attacks don't start with public buckets. They start with ABAC, tag abuse, and living-off-the-land AWS services. See how the real kill chain works.
S3 Ransomware Attacks: The S3 Heist Nobody's Talking About
The problem with most ransomware coverage? It starts at the ending.
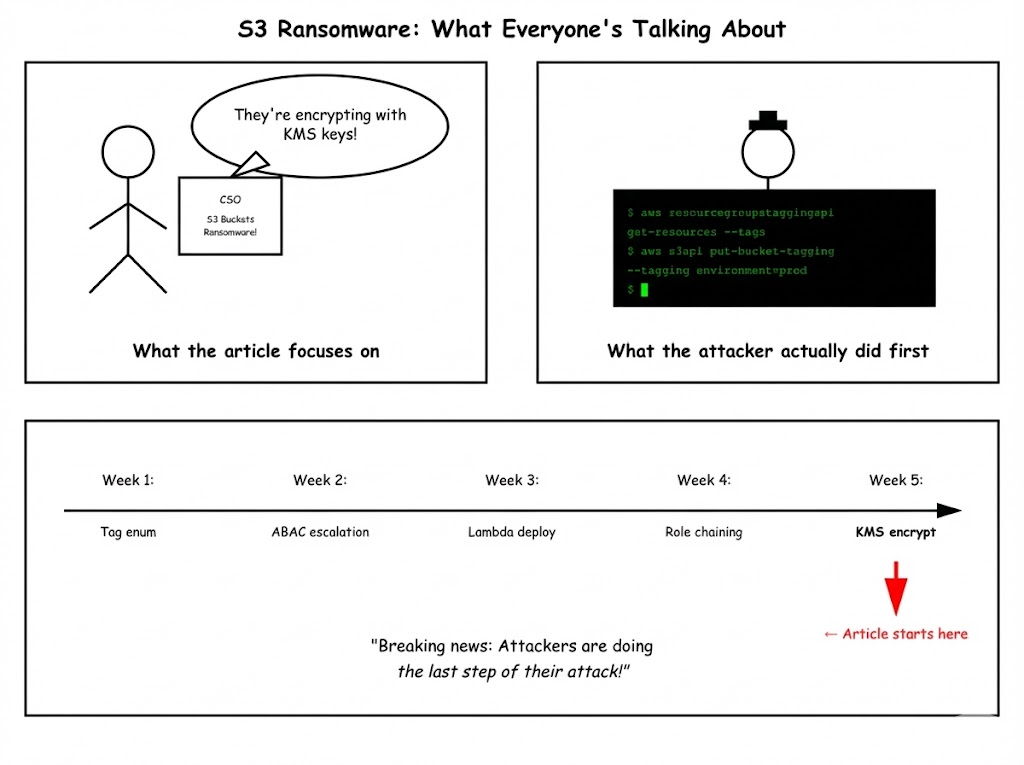
The recent wave of articles about ransomware gangs and other adversaries targeting cloud buckets reads like a mystery novel that opens with the final chapter. Yes, attackers are encrypting S3 data with AWS KMS keys and scheduling deletions. Yes, they're weaponizing customer-provided encryption (SSE-C) and external key stores. It's all very dramatic.
But here's what nobody's asking: How exactly did these attackers walk past your front door when cloud providers, and particularly AWS, made private S3 buckets the default years ago?
Spoiler alert: They didn't use a battering ram. They used your own cloud infrastructure as a ladder.
The Security Theater of "Safe by Default" S3
Let's give credit where it's due - AWS has genuinely improved S3 security baselines:
- Public buckets require explicit opt-in.
- Block Public Access is enabled by default.
- IAM policies are more restrictive.
- Your CSPM tool probably sends you a celebratory Slack notification every time it confirms these settings.
Meanwhile, sophisticated threat actors are not deterred by your compliance dashboard.
The uncomfortable truth? Modern S3 ransomware attacks don't start with misconfigured public buckets or stolen root credentials. They start with something far more insidious: AWS's own feature set, used exactly as designed or simply called abusing the context.
This is where ABAC, tagging, and identity design become part of the real S3 ransomware attack surface.
Why Amazon's New ABAC Feature for S3 Matters for Adversaries
Amazon recently rolled out ABAC (Attribute-Based Access Control) for S3 general purpose buckets. It is the latest security feature that can change the game from "bucket-name-policy" to "tag-key/value policy".
In plain English:
You no longer have to keep a separate IAM role per bucket. One policy that reads aws:ResourceTag/environment=development will grant GET, PUT and LIST permissions on any bucket that carries the same tag value.
How ABAC changes the S3 Attack Surface
| Feature | Attack vector | Exploitability Risk Impact |
|---|---|---|
| Tag-based policy | Use a single policy that grants s3:GetObject, s3:PutObject, s3:ListBucket to any principal whose IAM role contains the same tag key/value pair. | High |
| ABAC enabled bucket | The bucket itself becomes a policy target - it will read the policy's StringEquals condition and grant access if the tags match. | Critical |
| New ABAC API | PutBucketAbac and PutBucketTagging let you control the lifecycle in one command line. | Medium / High |
The benefit is two-fold:
- Scope: Attackers can now target all "environment:development" buckets in a single go (the attacker's "one-click kill chain").
- Speed: They can encrypt, delete and re-encrypt an entire bucket within minutes, because the policy reads its own tags.
The technical magic behind ABAC is simple enough that even a non-technical person can explain it:
- In the console, you enable ABAC under "Properties -> Permissions" on each bucket.
- You tag your bucket with one or more key/value pairs (e.g., environment=development).
- You write an IAM policy that checks for those tags, and grants permissions accordingly.
- Attackers can now read from any S3 bucket that has the same tag value.
In a S3 attack context, that means tag manipulation + ABAC = a stealthy path to large-scale data access.
The Real S3 Attacks Kill Chain: ABAC and the Art of Privilege Escalation
Here's where the ransomware narrative gets interesting, and where most security vendors conveniently stop explaining.
Attribute-Based Access Control (ABAC) was AWS's answer to IAM policy sprawl. Instead of maintaining hundreds of identity-based policies, you tag your resources and principals, then write elegant policies that match them dynamically. It's cloud-native. It's scalable. It's chef's kiss.
It's also a privilege escalation playground in the wrong hands.
Consider this scenario:
- A threat actor compromises an EC2 instance with minimal permissions - perhaps a development server running a vulnerable CI/CD agent.
- Nothing exciting. Your EDR barely shrugs. That instance has SSM agent installed (who doesn't?) and limited S3 access to "dev" environments via ABAC tags. Here's where the magic happens.
Now the S3 ransomware attack really begins.
The Tag Heist Nobody Sees Coming
The attacker doesn't need to steal admin credentials or exploit zero-days.
Instead, they:
- Use AWS's Resource Groups Tagging API to quietly enumerate which S3 buckets use ABAC.
- Time their reconnaissance during business hours, spreading API calls across regions to blend with legitimate traffic.
- Generate CloudTrail logs that look like normal read operations - nothing triggering alerts.
Next, they deploy an innocent-looking Lambda function via CloudFormation. The function name? Something like "automated-backup-system" or "compliance-audit-tool." Pick your favorite.
It requests permissions that sound reasonable: S3 bucket creation, tagging, basic management operations.
Your security team approves it. Why wouldn't they? It looks like standard DevOps automation.
That Lambda creates new S3 buckets in less-monitored regions (ap-south-1, anyone?), enables ABAC, and tags them as "environment: production." Through careful tag manipulation and role chaining, the attacker now has production-level access - without ever touching your actual production credentials.
That Lambda modifies the tags from a production S3 buckets and into "environment: dev". Using the initially compromised EC2 instance and through careful tag manipulation and role chaining, the attacker now has production-level access - without ever touching your actual production credentials. The lambda function can sit in another region.
Living Off the Land: AWS Services as Attack Tools
What makes this attack pattern devastating is its use of legitimate AWS services:
- AWS Glue
- Lake Formation
- Systems Manager
- Step Functions
Each service call looks justifiable in isolation. Your SIEM sees "authorized API activity" and moves on. No malware. No command-and-control traffic. Just AWS-native tooling doing what AWS-native tooling does.
By the time the attacker reaches the ransomware deployment phase - the part where they encrypt your S3 data with a KMS key they control and schedule its deletion - they're operating with permissions your IAM policies explicitly granted them through ABAC logic.
Why Your CSPM Can't See This Coming
Traditional cloud security tools excel at configuration validation. They'll alert you instantly if someone makes an S3 bucket public or disables encryption. They're fantastic at telling you what could go wrong.
They're terrible at proving what can actually be exploited.
Here's the gap:
- A CSPM might flag that your ABAC policies allow tag-based access escalation.
- But can an attacker actually exploit that configuration given your current IAM boundaries, SCPs, and permission boundaries? Does that theoretical attack path work when your VPC endpoints are configured? What about your SSM session policies?
Most security teams don't know. They're drowning in findings marked "High" and "Critical" that may or may not represent real risk. Meanwhile, adversaries are quietly testing which paths actually work.
From Theory to Reality: The Adversarial Validation Gap
This is where OFFENSAI's approach flips the script on AWS S3 buckets security misconfiguration risks.
Instead of scanning for what might be vulnerable, autonomous attack execution proves what is exploitable. Our platform operates like a threat actor under your current constraints - actual IAM policies, real network topology, existing security controls.
When OFFENSAI tests an ABAC privilege escalation path, it doesn't just check if the policy allows tag modification. It attempts the full attack chain:
- Can we enumerate ABAC-enabled resources?
- Do service control policies block our region-hopping technique?
- Will tag manipulation trigger GuardDuty or CloudTrail alerts your team actually monitors?
- Does the escalation path survive your permission boundaries?
The output isn't a list of theoretical CVEs scored by severity. It's proof-of-concept validation: "Here's the exact S3 focused attack chain that works in your environment today, with these three specific ABAC policies and S3 buckets, executed through this particular service combination."
The S3 Ransomware Endgame
So when ransomware operators finally reach the encryption phase - scheduling KMS key deletions, using customer-provided keys to lock you out, or leveraging external key stores - they're not exploiting a vulnerability.
They're using permissions you granted them, through a privilege escalation chain your security tools validated as "compliant," executed with techniques your detection rules never anticipated.
The majority of analyzes out there got the finale right: Attackers are weaponizing AWS encryption mechanisms for ransomware. But they buried the ledge.
The real story isn't that S3 buckets can be ransomed. It's that the path to that ransomware runs through your own cloud infrastructure, using features working exactly as your cloud provider designed them.?
Stop Just Scanning. Start Validating S3 Attack Paths.
Here's what keeps CISOs up at night: You can't fix what you can't prove. Your CSPM found 847 findings this quarter. Your vulnerability scanner flagged 3,000+ issues. Which ones can an attacker actually chain together to reach your production S3 data?
The answer shouldn't be "let's wait and see."
See how OFFENSAI validates real attack paths in your AWS environment.Because the next S3 ransomware article shouldn't be about your organization.



