Autonomous Cloud Attack Execution
Boost Your Cloud Security with AI
Replace sporadic and manual cloud testing with OFFENSAI's AI-powered Red Team automation platform built for continuous cloud security validation.
Dynamic Cloud Security Approach
Eliminate the Noise
Filter the background chatter and get only exploitable risks. Noise is distraction - we eliminate it.
Prioritize Attack Paths
Map chains together in your own cloud, and find the fastest way to stop attackers with one-click fixes.
Adapt with AI
Clouds shift daily. We continuously morph attack paths with fresh TTPs, validating against the latest adversary behavior.
See OFFENSAI In Action
Watch how OFFENSAI autonomously discovers and executes real attack paths in your cloud environment
Real Attack Paths, Real Results
Experience how OFFENSAI transforms complex cloud security testing into clear, actionable insights. Each attack scenario is presented step by step with rich visual support, showing exactly how an adversary would move through your environment. The live diagram updates in real-time, highlighting current attack phases, compromised resources, and potential impact as the autonomous red team validates each exploitation path.
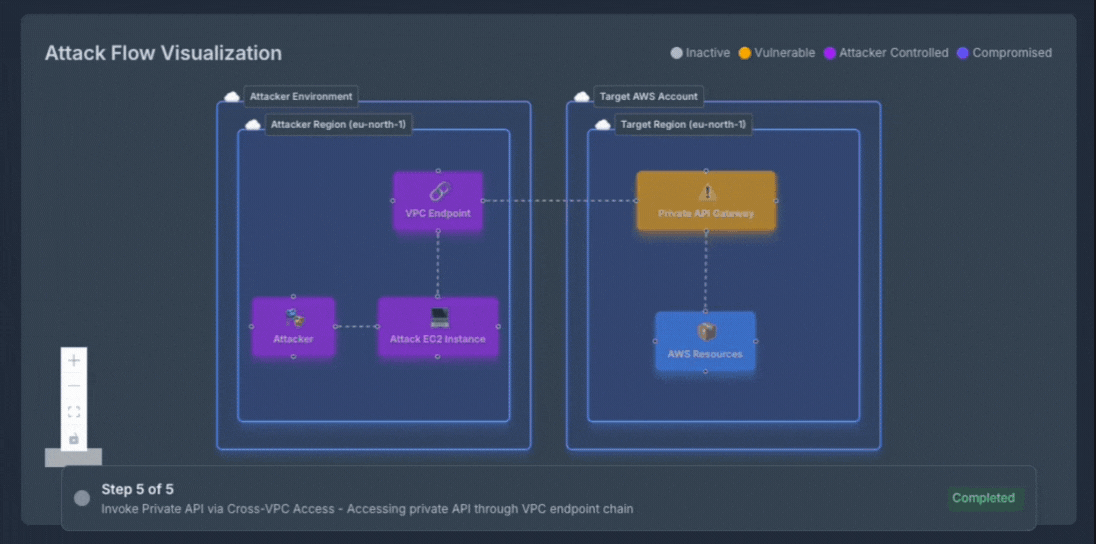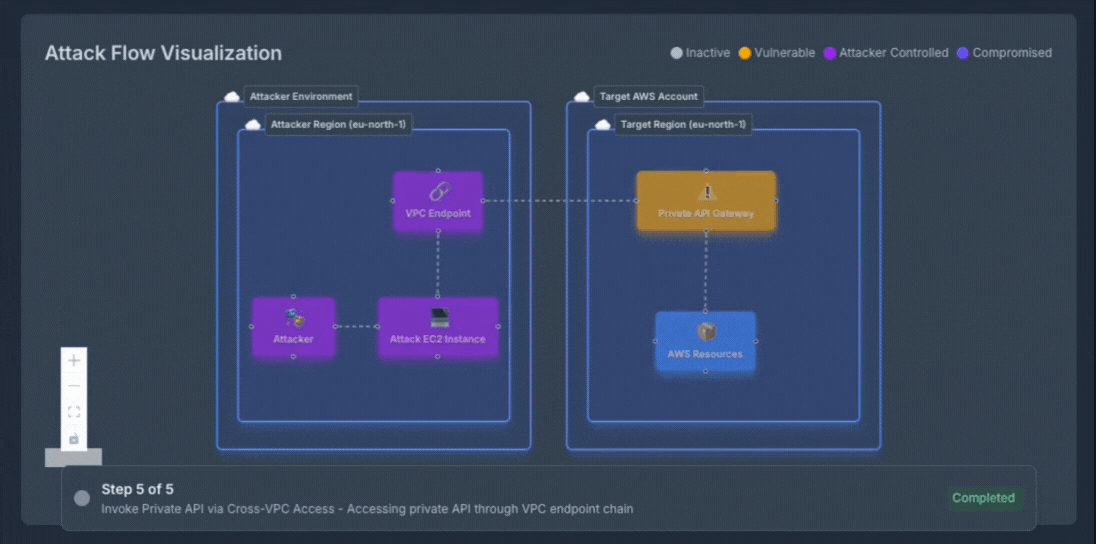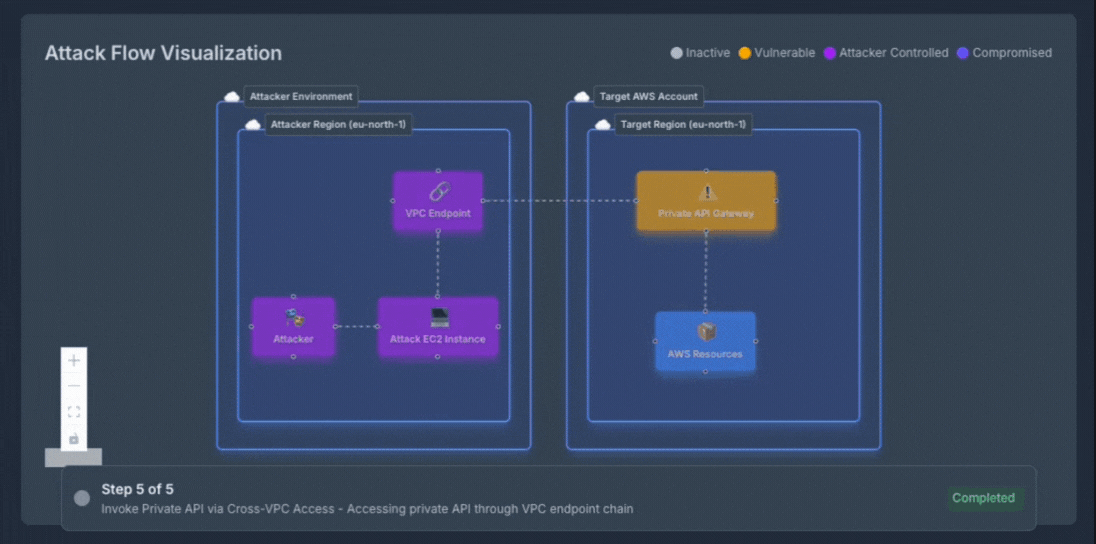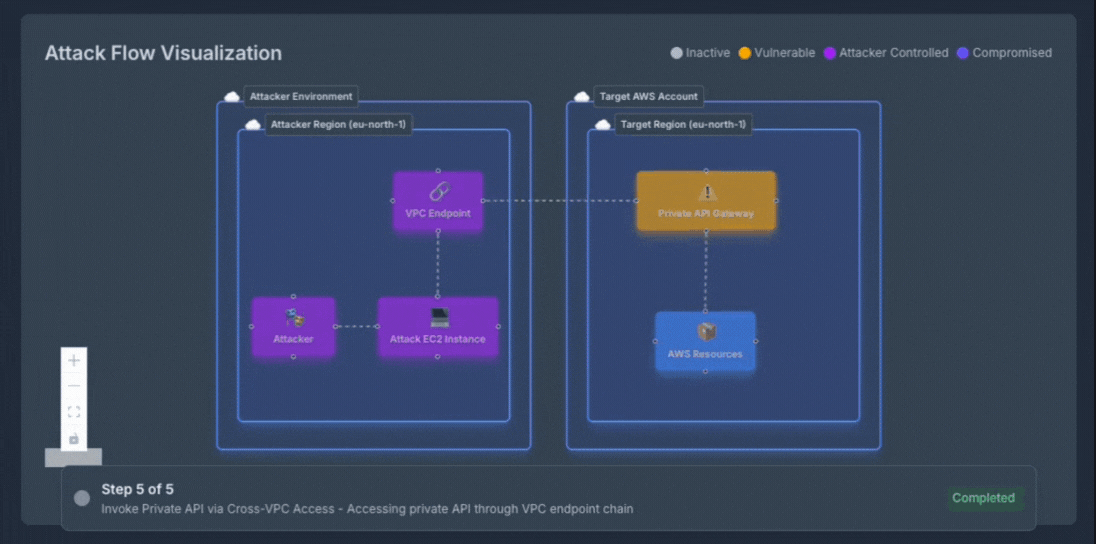
What You're Seeing
Define a new Cloud Security Standard
Agentless Setup
Real-World Risk Scoring Beyond CVSS
Unique Attack Vectors
Autonomous Attack Execution
One-Click Kill Chain Remediation
Adaptive AI Red Teaming
AI-powered Cloud-Native Intelligence
Audit-Ready Report & Compliance
The Real Modern Cloud Security Testing
Generative Attack Engine
Replace theoretical risk with executed kill chains, from initial entry, to lateral movement, and data exfiltration. Your team can uncover hidden cloud attack paths, stay ready for the unexpected, and strengthen defenses before adversaries strike.
Tactical Evasion Engine
Get better insights every time - OFFENSAI learns from every detection, then adapts its tactics to slip past your controls, just like real adversaries. By challenging your security with evolving evasion techniques, you know which controls actually trigger and where visibility gaps remain.
Morphed Attack Paths
If one path is blocked, it instantly tries another, and tries to get through, until coverage is complete - every move sharpens the next, feeds back into the AI's decision-making and reveals your weak spots real attackers would exploit, giving your team clear action.
Threat Intel
Every test is mapped to MITRE ATT&CK and enriched with the latest cloud-native TTPs - the result is realistic attack chains instead of canned checks, ATT&CK-aligned evidence you can use for training, reporting, and audits, and instant answers to "are we exposed to this?" whenever new threats emerge.
Reduce Real Cloud Breach Exposure
Give your team security validation that cuts through alert noise, confirms real risks, and strengthens your entire cloud environment.
24/7 Red Teaming
Continuously challenge your defenses and get better insights into your security posture without manual effort.
Adaptive Technology
Automatically discovers and reduces new attack surfaces as you deploy new resources, modify IAM policies or change network configurations.
Meet Compliance Proactively
Show SOC 2, NIST, and ISO 27001 auditors evidence of real-world control validation, not just checkboxes.
Test Your Cloud Defenses
Don't wait for a breach to learn your defenses have gaps, prove and improve them now. Continuously validate and fortify your cloud against real-world threats before they strike.



