Why Your CDK Security Is Failing: The Case for Continuous Cloud Attack Validation
Your security scanner flagged 847 findings in your AWS environment last week and...

Why Your CDK Security Is Failing: The Case for Continuous Cloud Attack Validation
Your team spent days triaging alerts about S3 bucket policies, overprivileged IAM roles, and CloudFormation execution permissions. But here's the question no CSPM tool can answer: Which of these issues can actually be chained together into a working attack?
This is where most cloud security approaches fail. They excel at finding misconfigurations but can't prove which ones matter in the real world. Meanwhile, your AWS CDK deployments are creating a web of interconnected vulnerabilities that traditional security tools were never designed to test.
The CDK Bootstrap Blind Spot: Where Theory Meets Reality
Every CDK deployment starts with cdk bootstrap - a command that 95% of engineers run with default settings, creating predictable infrastructure patterns that attackers love. Your security posture management tool will dutifully report:
- S3 bucket with predictable naming:
cdk-hnb659fds-assets-123456789012-us-east-1 - IAM role with AdministratorAccess policy attached
- Cross-account trust relationship configured
But what it won't tell you is whether an attacker can exploit these findings together to achieve account takeover. That requires actually testing the attack path - something traditional scanning tools simply don't do.
The Attack Chain Your Scanner Missed:
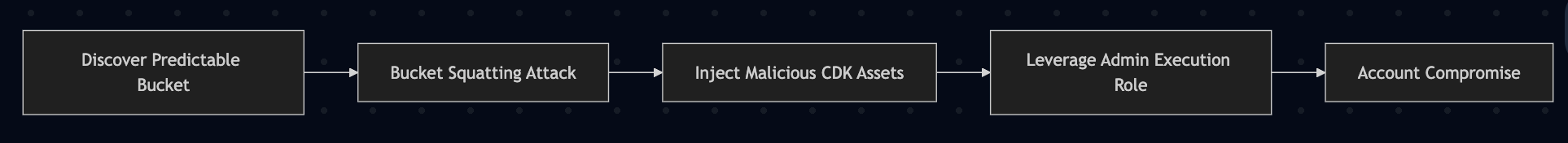
In June 2024, Aqua Security revealed that 1% of CDK users were vulnerable to complete account takeover through this exact vector. The scary part? Most organizations had no idea their "secure" CDK deployments were exploitable until someone actually tried to exploit them.
Why Configuration Scanning Isn't Enough
Traditional cloud security posture management (CSPM) tools operate on a fundamental assumption: if you fix all the misconfigurations, you'll be secure. But real-world attacks don't work that way. Consider this common CDK setup:
The "Secure" Configuration That Isn't
Your security dashboard shows green across the board:
- CloudFormation execution role has "least privilege" boundaries
- S3 buckets have encryption enabled
- Cross-account access follows approval workflows
But your environment is still compromised because your security tools missed the exploitation chain:
- Compromised CI/CD token (not in AWS scope)
- Assumes deployment role (legitimate action, passes all checks)
- Deploys backdoored StackSet (valid CloudFormation, just malicious)
- Propagates to all connected accounts (working as designed)
No amount of configuration scanning would have caught this because each individual step was "secure" - it's the combination that's dangerous.
The Multi-Account Multiplication Problem
Modern AWS architectures amplify these risks through complexity. A typical enterprise setup might include:
- Management Account: Controls StackSets, SCPs, and cross-account roles
- Security Account: Centralized logging and compliance monitoring
- Production Accounts: Customer-facing workloads
- Development Accounts: Rapid iteration and experimentation
Each account looks secure in isolation. But compromise the management account, and you can deploy malicious infrastructure to every connected environment - while your security tools continue showing green status across the board.
Attack Path Reality Check:
- Compromised GitHub Action Token →
- Management Account Admin Role →
- Malicious StackSet Deployment →
- Backdoors in All Production Accounts
Your CSCP tool will never test this end-to-end attack path because it doesn't actually attack anything.
The CloudFormation Execution Time Bomb
Here's what keeps CISOs awake at night: most CDK deployments use CloudFormation execution roles with AdministratorAccess policies. Security teams justify this as "necessary for deployment flexibility," but it creates a massive blast radius.
Common Misconfigurations That Compound:
| Component | Common Issue | Attack Vector |
|---|---|---|
| Bootstrap Role | AdministratorAccess policy | Complete privilege escalation |
| File Publishing | Overly permissive S3 access | Asset injection attacks |
| Cross-account Trust | No resource constraints | Lateral movement |
| OIDC Configuration | Weak claim validation | CI/CD compromise |
The problem isn't any single misconfiguration - it's how they combine to create exploitable attack paths that your security scanner will never discover because it doesn't actually test exploitability.
The Multi-Cloud Complexity Multiplier
As organizations extend CDK to manage Azure and GCP resources, the attack surface expands exponentially. Consider this "secure" multi-cloud pattern that looks secure, but creates cross-cloud attack path:
// new CfnCustomResource(this, 'AzureStorage', { type: 'Custom::AzureStorage', properties: { azureCredentials: secretsManager.secretValue } });
Your AWS security tools validate the CloudFormation template. Your Azure security tools check the storage configuration. But neither tests whether compromising the AWS Secrets Manager secret leads to Azure privilege escalation - which then enables AWS cross-account attacks via shared automation.
Why Traditional Validation Falls Short
Point-in-Time Testing:
- Annual penetration tests catch issues that existed months ago
- Quarterly red team exercises miss daily deployment changes
- Security assessments become obsolete as soon as new code deploys
Fragmented Tool Coverage:
- CSPM finds misconfigurations but doesn't prove exploitability
- CNAPP provides comprehensive monitoring but limited attack simulation
- Vulnerability scanners focus on software flaws, not on cloud control-plane attack paths
Alert Fatigue Reality: Teams receive hundreds of "critical" security findings weekly. Without proof of exploitability, everything gets the same priority - which means nothing gets prioritized effectively.
The Solution: Continuous Attack Validation
What if you could safely test whether your CDK deployments are actually exploitable? Not just scan for misconfigurations, but actually attempt the attack chains that matter?
This is exactly what OFFENSAI’s Autonomous Cloud Attack platform provides:
Continuous Validation Benefits:
- Proof of Impact: Shows which misconfigurations are actually exploitable
- Attack Path Discovery: Reveals complex chains that span multiple services
- Priority Intelligence: Focuses remediation on issues that matter based of you business vertical context
- Real-World Context: Tests defenses against actual attacker techniques
The Crash Test Approach: Just as car manufacturers don't just inspect vehicles - they crash test them - modern cloud security requires actually testing your defenses against real attack techniques.
How Continuous Cloud Attack Validation Can Help
Phase 1: Baseline Attack Simulation Start with common CDK attack vectors & beyond:
- Bootstrap bucket exploitation
- CloudFormation execution role abuse
- Cross-account privilege escalation
- CI/CD pipeline compromise
Phase 2: Multi-Account Attack Paths Test complex scenarios:
- StackSet-based lateral movement
- Cross-account data exfiltration
- Management account compromise impacts
Phase 3: Multi-Cloud Integration Validate end-to-end security:
- AWS-to-Azure attack chains
- Shared credential exploitation
- Cross-cloud privilege escalation
The Business Case for Attack Validation
Risk Reduction:
- Identify exploitable vulnerabilities before attackers do
- Validate that security controls actually work under attack
- Reduce time from vulnerability discovery to remediation
Operational Efficiency:
- Focus remediation efforts on proven threats
- Reduce alert fatigue through prioritized findings
- Automate continuous security validation
Compliance Benefits:
- Demonstrate active security testing to auditors
- Provide evidence of control effectiveness
- Meet evolving regulatory requirements for continuous monitoring
Beyond Configuration Management: Testing What Matters
The complexity of modern CDK deployments stems from accumulated convenience compromises. Each "temporary" admin permission or hardcoded secret becomes a permanent attack vector that traditional security tools will never find because they don't actually test exploitation.
The Path Forward:
- Implement Continuous Attack Simulation: Test your CDK deployments against real attack techniques
- Validate Defense Effectiveness: Prove your security controls work under pressure
- Prioritize Based on Exploitability: CVE is broken. Focus on issues that actually matter from your business context not general overview.
- Automate Security Validation: Make attack testing as routine as deployment testing
Conclusion: From Hope to Proof
Traditional cloud security asks you to hope your configurations are secure. Modern cloud security demands proof.
Your CDK deployments are creating complex, interconnected systems that no human can fully understand, and no static scanner can completely validate. The only way to know if they're truly secure is to safely attack them yourself - before someone else does it maliciously.
The question isn't whether your cloud infrastructure has vulnerabilities - it's whether you'll discover them first through controlled testing, or learn about them during an actual breach.



